A group of random character .XYZ domains was utilized in a phishing attack that lasted for several months.
Last August, attackers initiated a phishing campaign with emails that masqueraded as Xerox scan notifications, prompting users to open a malicious HTML attachment. The attack successfully bypassed Microsoft Office 365 Advanced Threat Protection (ATP) filtering and stole over a thousand corporate employees’ credentials.
Checkpoint reports that the method used by the cybercriminals left behind a trail of information that was mistakenly allowed access by Google that scanned lists of stolen credentials. In essence, all of the criminals’ “hard work” was accessible via simple Google searches.
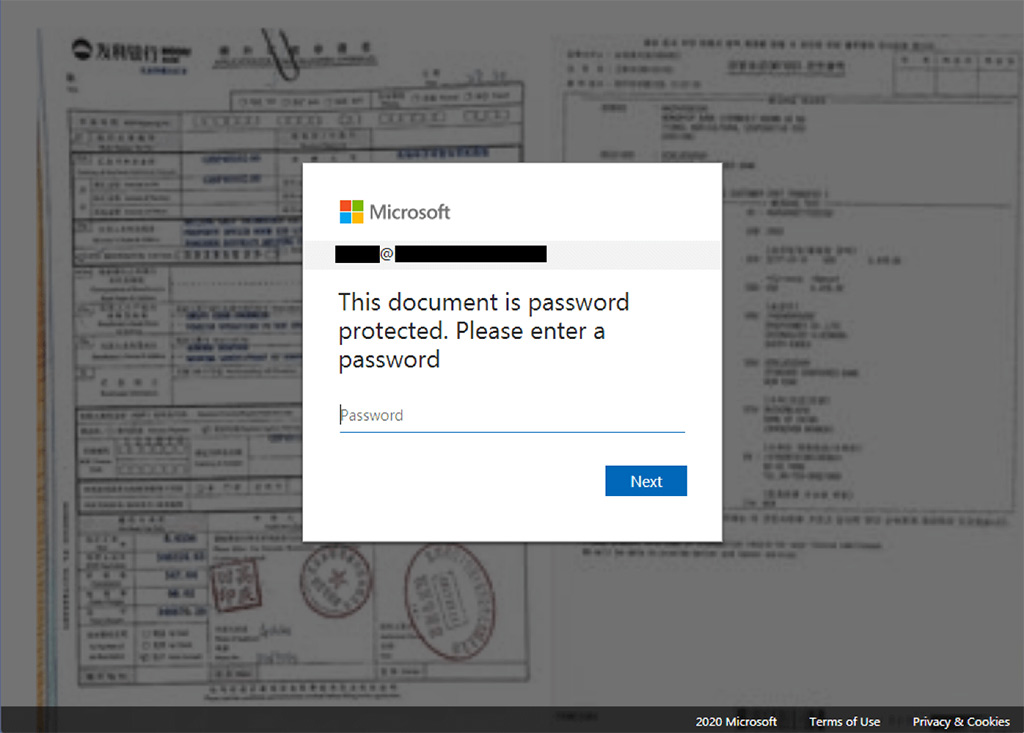
Here’s a list of the .XYZ domains used in the attack, per Checkpoint’s researchers:
Copyright © 2025 DomainGang.com · All Rights Reserved.aauths.xyz
asklogzswq.xyz
bdqopt.xyz
drakovexlogz.xyz
hrekre.xyz
ionlineforyou.xyz
itsthebestasajob.xyz
khetwexw.xyz
livestrde28.xyz
loggsofice.xyz
manonwork.xyz
officeautonow.xyz
officednslogsonline.xyz
quantityscape.xyz
redirectitto.xyz
rhbreeef.xyz
sendlivofse.xyz
shlivemicrosft.xyz
synchoilas.xyz
urentr.xyz
vintageredwe.xyz
wegoforyou.xyz
weworkhard.xyz
workingoni.xyz
zixzanwe.xyz
mtietw.xyz
justgoturwork.xyz
froffisse.xyz