DNS abuse is defined as any malicious activity aimed at disrupting the DNS infrastructure or causing the DNS to operate in an unintended manner. The functionality of domain names depends on addressing such DNS abuse issues.
Mitigating DNS abuse is important as it’s an increasingly thorny issue for registries and registrars worldwide. Solving it or mitigating its effects requires a joint effort and centralized functions and coordinated activities among the stakeholders.
Compromised vs. maliciously registered domain names.
Defining DNS abuse is essential to make a clear distinction when discussing “abused” domain names.
Domains registered with the deliberate intention to harm: Is the domain registered maliciously? To answer this question, you could visit the website and see if valuable and trustworthy content is available. Then, check the WHOIS database. If the domain was registered only a few days before it got blacklisted, then a red flag should be going up.
Domains of hacked websites used to harm: Domain names might have been registered legitimately. The website gets compromised to serve illegal content and phishing campaigns. The legitimate domain names are usually registered many years before and the domain name is valid.
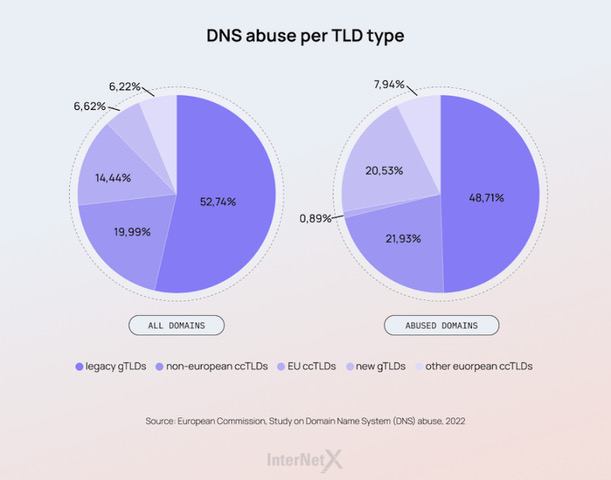
What TLDs get most abused?
At the end of January 2022, the European Commission published a report on DNS abuse. To assess the impact of DNS abuse, the authors conducted an overall health check of the top-level domain (TLD) ecosystems.
- In relative terms, the most abused TLDs are new gTLDs.
- The two most abused new gTLDs account for 41% of all abused new gTLD domain names, which means that not all new gTLDs experience DNS abuse to the same extent.
- European ccTLDs are the least abused domain names in absolute terms.
- Most spam and botnet command-and-control domain names are maliciously registered. Legitimate users registered about 25% of phishing domain names and 41% of malware distribution domain names. They were compromised at the hosting level.
- The top five most abused registrars account for 48% of all maliciously registered domain names.
- The general adoption of DNSSEC remains low.
Simone Catania—Global Content & Communications Manager at InterNetX—explains why defining DNS is so complicated and describes existing scenarios for prevention and mitigation.
Read the full article titled “The debate around defining, preventing and mitigating DNS Abuse. ”
Copyright © 2025 DomainGang.com · All Rights Reserved.