Escrow.com was briefly defaced, after its DNS was pointed to an IP address in Malaysia, and the incident was made possible by accessing its managing account at GoDaddy.
The hacker registered the domain ServiceNow-GoDaddy.com and was able to craft a convincing email, that fooled a GoDaddy employee. They also obtained a free SSL certificate from Let’s Encrypt that assisted with the eventual defacement.
The spoof domain’s registration was fundamental in facilitating this advanced hacking attack; Service Now is a cloud services provider that is used by GoDaddy. They provide a portal for such services at the subdomain GoDaddy.Service-Now.com.
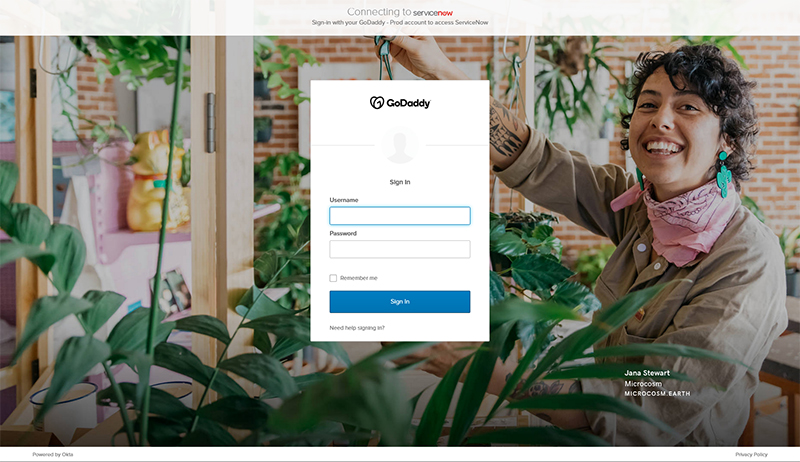
The hacker reversed that pair of keywords by registering the domain, and a GoDaddy employee, most likely working from home, logged into the portal and surrendered that account’s credentials.
It’s fascinating to read what followed:
The Escrow.com domain at GoDaddy was secured by means of containing further notes that instructed the placement of a phone call, presumably to unlock the domain if needed.
The hacker called the number, believing it’s still talking to GoDaddy, when in fact it was the Escrow.com general manager on the other end of the line!
Krebs on Security has a detailed report on the incident, that provides additional references to how Escrow.com data and its clients were not affected.
Some view this embarrassing incident as a failure of Escrow.com to safeguard its domain, when in fact it was a case of social engineering that gave up the account’s credentials at the Registrar, GoDaddy.com.
Important: Current conditions mandate that companies transition their employees to home based offices. Security alone is not enough: All staff needs to be alert at all times and be aware of malicious attempts to obtain private information via social engineering and other phishing techniques.
Copyright © 2025 DomainGang.com · All Rights Reserved.