A group of six individuals were charged with computer crimes related to their alleged ownership of services facilitating Distributed Denial of Service (DDoS) attacks.
These services provided “for hire” attacks on demand to anyone willing to pay money to perform electronic warfare on internet destinations and web sites.
Each defendant allegedly operated at least one website that offered one-stop services and subscriptions of various lengths and attack volumes. In each of these criminal cases, the FBI posed as a customer and conducted test attacks to confirm that the booter site functioned as advertised.
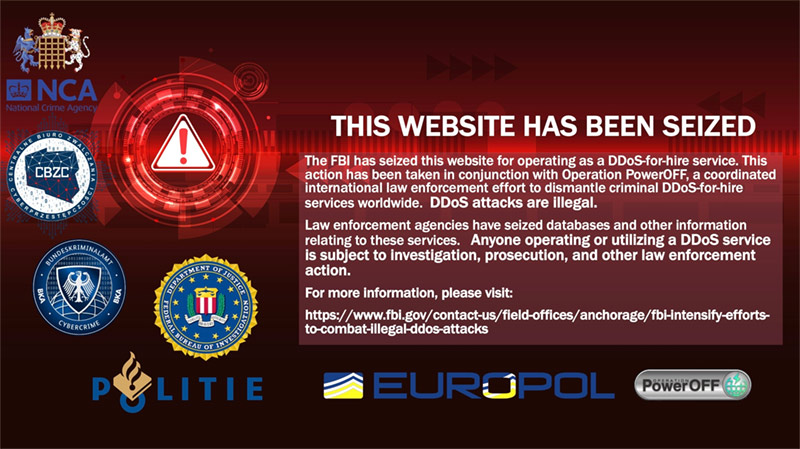
In the process, 48 domains were seized or are otherwise being seized by the US Department of Justice:
api-sky.xyz
astrostress.com
blackstresser.net
booter.sx
booter.vip
bootyou.net
brrsecurity.org
buuter.cc
cyberstress.us
defconpro.net
dragonstresser.com
dreams-stresser.io
exotic-booter.com
freestresser.so
instant-stresser.com
ipstress.org
ipstress.vip
ipstresser.com
ipstresser.us
ipstresser.wtf
ipstresser.xyz
kraysec.com
mcstorm.io
nightmarestresser.com
orphicsecurityteam.com
ovhstresser.com
quantum-stresser.net
redstresser.cc
royalstresser.com
securityteam.io
shock-stresser.com
silentstress.net
stresser.app
stresser.best
stresser.gg
stresser.is
stresser.net
stresser.org
stresser.one
stresser.shop
stresser.so
stresser.top
stresserai.com
sunstresser.com
supremesecurityteam.com
truesecurityservices.io
vdos-s.co
zerostresser.com
We can see the full range of TLDs and ccTLDs, including .com, .net, .org, .app, .xyz, along with .us, .gg, .io and more.
The list of domains involved in criminal activity was shared by investigative reporter Brian Krebs, founder of KrebsOnSecurity.
Copyright © 2025 DomainGang.com · All Rights Reserved.