In the past year and a half, a lot of domain names were stolen from their lawful owners by phishing emails.
By sending emails posing as legitimate communication from a domain registrar, cybercriminals manage to obtain a domain owner’s user name and password.
Without two way authentication enabled at the registrar level, one is at risk of losing access to their account, and domain names.
Taking this approach one step further, the use of social engineering can compromise the existence of two way authentication.
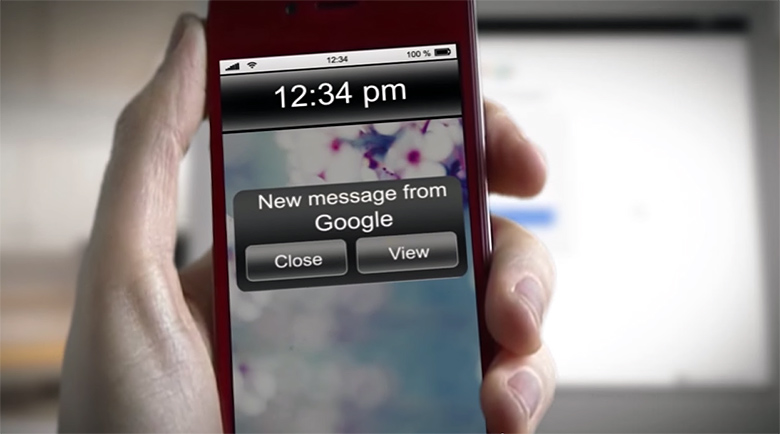
Cybercriminals use SMS as a method of social engineering.
A method used to obtain access to Gmail accounts, many of which are used to manage domains, is explained in this video by security experts Symantec.
The cybercriminal needs to know your email and mobile phone number and initiate a password reset process involving the use of SMS to reset the password.
Moments later, they send an SMS to your phone, stating that there is a security issue with your account, and asking for the code that’s already sent by Gmail.
Never respond to such SMS prompts to send back a message; the sender is quite often easy to spoof and make it appear as if the message was sent by Gmail.
For the full video explaining the process, watch the Symantec video below.
Copyright © 2025 DomainGang.com · All Rights Reserved.









I decided early on that my cell phone is for phone calls, so I turned off SMS altogether.
Haven’t missed it one bit — I avoid a lot of BS.
I don’t use my mobile for Whois info either.
🙂